“Right after I graduated, I interned with the Arms Control Association. It was terrific.”
Probabilistic Verification: A New Concept for Verifying the Denuclearization of North Korea
September 2019
By Mareena Robinson Snowden
Although U.S.-North Korean talks have stalled, North Korean leader Kim Jong Un has abided by an apparent moratorium on nuclear testing, keeping alive hopes that an agreement can be reached to denuclearize North Korea. Implementing such an agreement with North Korea, if one can be negotiated, would constitute an unprecedented challenge for the international community.
 Verifying such an agreement would require building a monitoring regime that goes well beyond traditional international safeguards and bilateral arms control approaches while accommodating legitimate North Korean concerns over intrusiveness, which would practically preclude “anytime, anywhere” inspections. Creativity will be needed to design a verification scheme to which the United States and North Korea could agree and that could be implemented in affordable and practical ways and that politicians would deem credible.
Verifying such an agreement would require building a monitoring regime that goes well beyond traditional international safeguards and bilateral arms control approaches while accommodating legitimate North Korean concerns over intrusiveness, which would practically preclude “anytime, anywhere” inspections. Creativity will be needed to design a verification scheme to which the United States and North Korea could agree and that could be implemented in affordable and practical ways and that politicians would deem credible.
Verification is the means by which parties to an agreement assure themselves that the agreement is being implemented faithfully. A central tension lies at the heart of verification: the need to balance confidence on one side with the sensitivities regarding intrusive monitoring on the other. In nuclear activities negotiations, verification traditionally has been accomplished through two means: international safeguards inspections on fissile material production and bilateral arms control monitoring of nuclear delivery vehicles, such as missiles and bombers. Both systems focused narrowly on just a few activities or items intrinsic to nuclear weapons and constructed monitoring approaches that would provide high confidence of detecting noncompliance.
Over time, the distinctions between these two types of verification regimes have blurred as some states pursued clandestine nuclear weapons programs. In South Africa in 1990, Iraq after 1992, and Libya in 2003, the International Atomic Energy Agency (IAEA) undertook activities that went beyond the narrow confines of fissile material accountancy to verify that all three states had ceased nuclear weapons-related activities. More recently, the IAEA investigated “possible military dimensions” of Iran’s nuclear activities, including experiments related to nuclear weapons design and testing.
The North Korean verification challenge is more substantial than these prior examples. Complete, irreversible denuclearization would require defining and implementing “disarmament” of a whole category of weapons and the pertinent infrastructure to develop, produce, and upgrade them—in real time. Still, as challenging as nuclear verification in North Korea may be, these historical approaches and ad hoc innovations offer lessons on how to design an approach that can work in North Korea. Experience from other verification regimes, such as the Chemical Weapons Convention, also can be helpful.
A Unique North Korean Verification Challenge
North Korea’s unique challenge demands innovation in the way verification is approached in practice and is conceived in theory. Since the inception of nuclear arms control and international safeguards, decision-makers, particularly in the United States, tended to frame international treaties and their associated verification regimes in binary terms akin to law enforcement: either actors are complying with the terms of the treaty or not. This legalistic view is reinforced by the belief that adherence to all parts of an agreement demonstrates the intent and trustworthiness of the participants. By extension, unwillingness to tolerate even low-level violations, regardless of military significance, signaled parties’ resolve to detect everything, hold each other accountable, and deter cheating.
This framing of verification narrows the scope of what an agreement can cover. To provide the desired near-certain confidence in monitoring compliance, the verification system must cover fewer activities in a more limited geographic area. This narrow scope served a related purpose in the case of U.S.-Soviet arms control, namely to limit reciprocal inspections and monitoring activity in order to protect national security information and mitigate other security concerns. The consistently narrow focus on missiles and their associated launchers in the last three U.S.-Soviet and U.S.-Russian nuclear arms control agreements—the Intermediate-Range Nuclear Forces (INF) Treaty of 1987, the Strategic Arms Reduction Treaty (START I) of 1991, and New START of 2010—reflects these considerations.
Achieving the complete denuclearization of North Korea, however, will require negotiators to take a broader view of proscribed activities and items. The tendency of negotiators to focus on easily verified items or activities will be too minimalistic. In addition to monitoring fissile material and nuclear missiles, as done under traditional approaches, a denuclearization regime will need to account for weapons research and development and military-related activities. Additionally, it will need to provide flexibility to resolve inevitable confusion around ambiguous behavior by North Korea.
 For these reasons, U.S. insistence on a traditional verification framework in negotiations with North Korea—implicit in the U.S. goal of final, fully verified denuclearization in North Korea—does not match the scope of the challenge, nor does it provide negotiators the flexibility needed to reach meaningful agreement. North Korea’s reported resistance to providing an up-front comprehensive declaration of its nuclear program for fear of creating a “target list” shows the need for a new approach.1 The picture is complicated further by the high probability that North Korea will insist on retaining at least some nuclear weapons until the very end of the denuclearization process, as well as missiles that can carry nuclear or conventional warheads. Moreover, given its penchant for secrecy and extreme concerns about regime stability, North Korea probably would not permit on-demand access to sensitive facilities, especially military bases. Beyond resistance by the regime, verifying denuclearization within North Korea also presents specific operational challenges that increase complexity: a poor infrastructure that constrains energy supply, inadequate roads and transportation, risks to the health and safety of inspectors, and topography and tunneling capability that is conducive to the concealment of major items.
For these reasons, U.S. insistence on a traditional verification framework in negotiations with North Korea—implicit in the U.S. goal of final, fully verified denuclearization in North Korea—does not match the scope of the challenge, nor does it provide negotiators the flexibility needed to reach meaningful agreement. North Korea’s reported resistance to providing an up-front comprehensive declaration of its nuclear program for fear of creating a “target list” shows the need for a new approach.1 The picture is complicated further by the high probability that North Korea will insist on retaining at least some nuclear weapons until the very end of the denuclearization process, as well as missiles that can carry nuclear or conventional warheads. Moreover, given its penchant for secrecy and extreme concerns about regime stability, North Korea probably would not permit on-demand access to sensitive facilities, especially military bases. Beyond resistance by the regime, verifying denuclearization within North Korea also presents specific operational challenges that increase complexity: a poor infrastructure that constrains energy supply, inadequate roads and transportation, risks to the health and safety of inspectors, and topography and tunneling capability that is conducive to the concealment of major items.
All of this amounts to the need to adopt an approach to denuclearization and its verification that is appropriate to this unique combination of challenges and allows for the broad prioritization of key activities and items of military significance. Shifting from the traditional to a probabilistic approach to verification could help negotiators address these challenges and diminish the likelihood that verification becomes an insurmountable obstacle to an agreement.
A Probabilistic Approach to Verification
For a denuclearization agreement to be comprehensive, it would need to prohibit or restrict a broad array of activities and capabilities beyond fissile material production. An associated verification regime requires a high probability of detecting a violation of one or more proscribed activities in time to allow an international response before North Korea could gain a military advantage from the violation. Achieving this target would not require 100 percent confidence that compliance with each and every term of the agreement can be verified. Rather, 100 percent confidence is needed that violation of at least one significant term will be detected in time. This is a critical distinction: though different in its theoretical approach, probabilistic verification in practice can still yield the high confidence required by policymakers in compliance assessments.
Probabilistic verification meets international security needs in situations where perfect or near-perfect verification arrangements are not possible, either because they cannot be imposed on one or more of the parties or because physical or fiscal realities do not allow them. Whereas traditional nuclear verification has focused on one or two readily observable objects or behaviors, such as missile dismantlement efforts or the nonoperation of plutonium-production reactors, probabilistic verification would encompass the many more capabilities and activities that enable a country to build and deploy a nuclear arsenal. In addition to fissile material production, this would cover weapons research and development, delivery vehicle production and systems integration, and military induction of nuclear weapons. This approach draws on the Carnegie Endowment for International Peace’s Nuclear Firewall Project, which identifies key technical and contextual indicators across the range of activities required to develop a nuclear arsenal as a means of distinguishing weapons-related programs from peaceful ones, whether in the context of nonproliferation or nuclear rollback.
The benefit of probabilistic verification comes from an aggregation of detection probabilities that provides an overall monitoring confidence across the full range of activities required for nuclear weapons. Monitoring confidence is a judgment made by nuclear negotiators and the intelligence community about the ability of a monitoring technology to achieve its stated objective.2 For example, if a ban on static rocket motor testing was ever to be negotiated as part of a denuclearization deal between the United States and North Korea, infrared satellite imagery would likely be included as a monitoring technology. As part of this future deal, North Korea would agree not to interfere with remote information gathering by using shields and other masking approaches. The ability of the satellites to observe covert motor tests would be based on how well and how frequently the satellite system was able to observe key zones of interest.
Assessing confidence in monitoring capability can vary based on a number of factors. For example, how effectively an indicator of noncompliance can rise above the background noise of other information will affect confidence in that indicator. The maturity of a monitoring technology will influence its perceived reliability, while its incorporation in previous verification regimes will affect its perceived negotiability. The timeliness of the result will directly affect whether the inspecting state is able to respond to a potential violation before it approaches the threshold of military significance. In the case of satellite-based monitoring of static rocket motor testing, the confidence judgment would be high, based on overall advances in spatial, temporal, and spectral resolution of satellite technology, the increased timeliness of image delivery, and the familiarity with satellite use as a proven information-gathering technology in a military and verification context.
Probabilistic Verification in Practice
A future denuclearization deal would need to monitor a broad range of activity in a variety of technical and military domains simultaneously in order to provide the international community adequate assurance of an end to the North Korean nuclear threat. Some activities for which there are established verification procedures, for example, fissile material production activities traditionally inspected by the IAEA or the deployment of nuclear delivery vehicles under the New START verification protocol, would be relatively straightforward to monitor.
How should negotiators think about the monitoring of activities not historically covered under nuclear agreements, such as the decoupling of warheads from missiles or a ban on weaponization activities and production of large rocket engines? Verifying the absence of such activities would be crucial to ensuring progress toward denuclearization, yet would require a level of access and intrusiveness that has not been negotiated in any previous arms control or international safeguards agreement. A notable exception here pertains to weapons design and development activities proscribed under Section T of the Joint Comprehensive Plan of Action agreement with Iran, the implementation of which by the IAEA has proven complicated.3 Negotiators would seem to face a choice between omitting weapons-relevant activities because the probability of detecting noncompliance on each and every activity is low or proscribing these activities and accepting that cheating on some may not be detected. In reality, though, a probabilistic verification system makes the latter option clearly preferable and overall more valuable than the traditional approach.
Generically speaking, in traditional and probabilistic verification regimes, some activities are exceptionally important and must be verifiable with high confidence. Examples could include plutonium production, uranium enrichment, and nuclear explosive testing. Under a probabilistic system, these top-tier activities would be supplemented with the monitoring of a range of other activities or capabilities deemed militarily significant, such as hydrodynamic explosions or static rocket motor testing. Even if 100 percent confidence in verification of these activities is not possible, they still merit proscription.
The innovation here is in shifting the focus of nuclear negotiations to overall monitoring confidence: the ability to detect violation in at least one monitored activity rather than confidence in detecting cheating on every proscribed activity.4 With this flexibility, negotiators can find agreement on a collection of monitoring activities that meets the U.S. requirement for a high overall monitoring confidence while providing a broader range of verification options to offer should North Korea object to any single approach during negotiation. Further, inclusion of activities with medium or low monitoring confidence does not incentivize cheating. In fact, probabilistic verification introduces an additional benefit by expanding the North Korean perception of the risk of cheating to a much broader range of activities that would be critical for sustaining a parallel program or a reconstitution capability.
As shown in table 1, the aggregation effects in a monitoring regime mean that the probability of detecting violation in at least one activity (Pat least one) increases as the number of monitored activities (i) increases. So even in cases where the majority of monitored activities are judged to be of low confidence, for example, in an inspector’s ability to monitor weaponization activities, increasing the number of monitored activities drives up the overall likelihood of detecting violation in at least one. This approach assumes that the probability of detecting violation in any one given activity is independent from others in the collection of monitored activities and items.
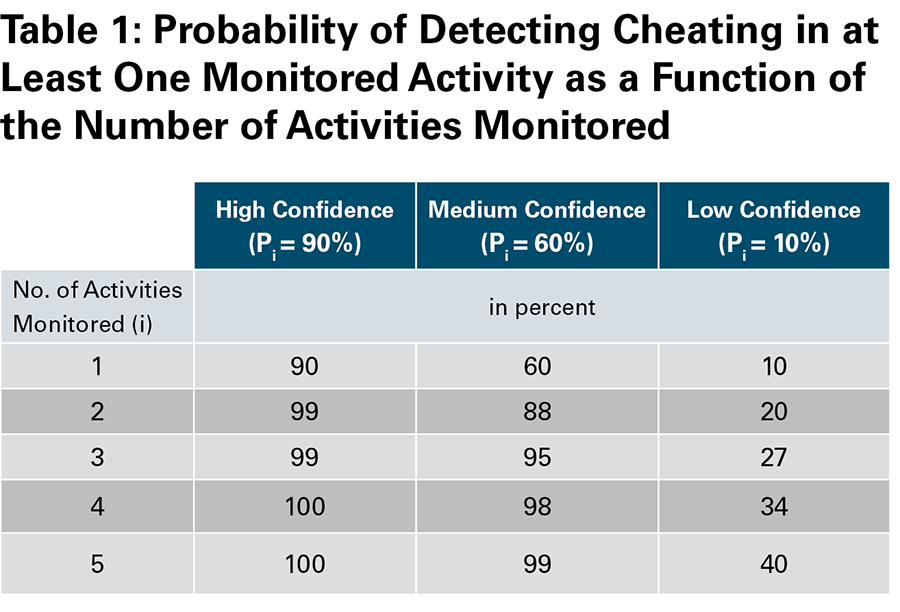 Verification experts may debate what constitutes low-, medium-, or high-confidence levels, but the important shift introduced by a probabilistic view on verification is the prioritization of deterrence value alongside detection probability. The U.S. intelligence community treats monitoring technologies with no better than a 50 percent chance of detecting violation, or with 50 percent uncertainty in a measured quantity, as low confidence.5 Yet, this perspective ignores the deterrent value of wide-scale, multimethod monitoring. For state leaders debating whether to cheat on a nuclear deal, a 50 percent chance of being detected is likely perceived as quite high and would be an important consideration in decisions to cheat in a militarily significant way.
Verification experts may debate what constitutes low-, medium-, or high-confidence levels, but the important shift introduced by a probabilistic view on verification is the prioritization of deterrence value alongside detection probability. The U.S. intelligence community treats monitoring technologies with no better than a 50 percent chance of detecting violation, or with 50 percent uncertainty in a measured quantity, as low confidence.5 Yet, this perspective ignores the deterrent value of wide-scale, multimethod monitoring. For state leaders debating whether to cheat on a nuclear deal, a 50 percent chance of being detected is likely perceived as quite high and would be an important consideration in decisions to cheat in a militarily significant way.
In practice, it would be the job of the negotiating delegations, through the use of expert input from the technical, intelligence, and policy communities, to prioritize the activities and items to be included in the monitoring portfolio and estimate the likelihood of detection for each approach. The figure below shows representative examples of portfolio configurations at either end of the confidence spectrum and illustrates that even when activities outside of traditional verification practice are included, high overall monitoring confidence can be achieved. This alternative perspective sees value in the inclusion of activities and technologies that would be disregarded under a traditional verification framework, understanding that deterrence value should be considered alongside the overall confidence of a monitoring technology.

Conclusion
The advanced state of the North Korean military nuclear program, coupled with the unique nature of U.S.-North Korean relations, makes the denuclearization verification challenge unlike anything the international community has faced. Traditional approaches alone, safeguards and arms control monitoring, will not provide the coverage needed to confidently assess the elimination of the North Korean nuclear threat, nor are they likely to prove negotiable with North Korea. Thus, the North Korean verification challenge requires innovative thinking and problem solving well beyond the bounds of traditional verification approaches.
Critically, verification must be negotiated hand-in-hand with proscriptions on activities. Verification considerations should guide the prioritization of activities to limit, but in a way that broadens the scope and creates flexibility for how such limitations might be verified over time. If Pyongyang accepts proscription of an activity or technology, it would be foolish not to proscribe it merely because North Korea objects to a particular verification approach. The history of breakdowns in the 1994 Agreed Framework with North Korea and the later six-party talks, largely over differences of view on verification, underscores the importance of synergy between limitations and monitoring approach. A more flexible approach to verification, one that preserves monitoring confidence, provides negotiators with more options, and more fully contains the qualitative and quantitative improvements to North Korea’s nuclear program, is the best chance to provide sufficient verification and, over time, help create conditions under which North Korea would fully disarm.
ENDNOTES
1. “Trump to Meet With Kim Jong-un, Despite North Korea’s Lapses, Bolton Says,” The New York Times, December 4, 2018.
2. Howard Stoertz Jr., “Monitoring a Nuclear Freeze,” International Security, Vol. 8, No. 4 (Spring 1984): 95.
3. See Jarrett Blanc, “There Is No Crisis in JCPOA Section T,” Carnegie Endowment for International Peace, October 17, 2017, https://carnegieendowment.org/2017/10/17/there-is-no-crisis-in-jcpoa-section-t-pub-73454.
4. The probability of detecting violation in at least one proscribed activity is 1-Pnone=1-∏i1-Pi, where Pi is the violation detection probability in activity/item i.
5. Stoertz, “Monitoring a Nuclear Freeze,” p. 95.
Mareena Robinson Snowden is a senior engineer at the Johns Hopkins University Applied Physics Laboratory. Prior to this, she served as a Stanton Nuclear Security Fellow at the Carnegie Endowment for International Peace, where her research focused on nuclear arms control verification, nonproliferation, and modernization.
